Kejahatan siber pdf sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset.
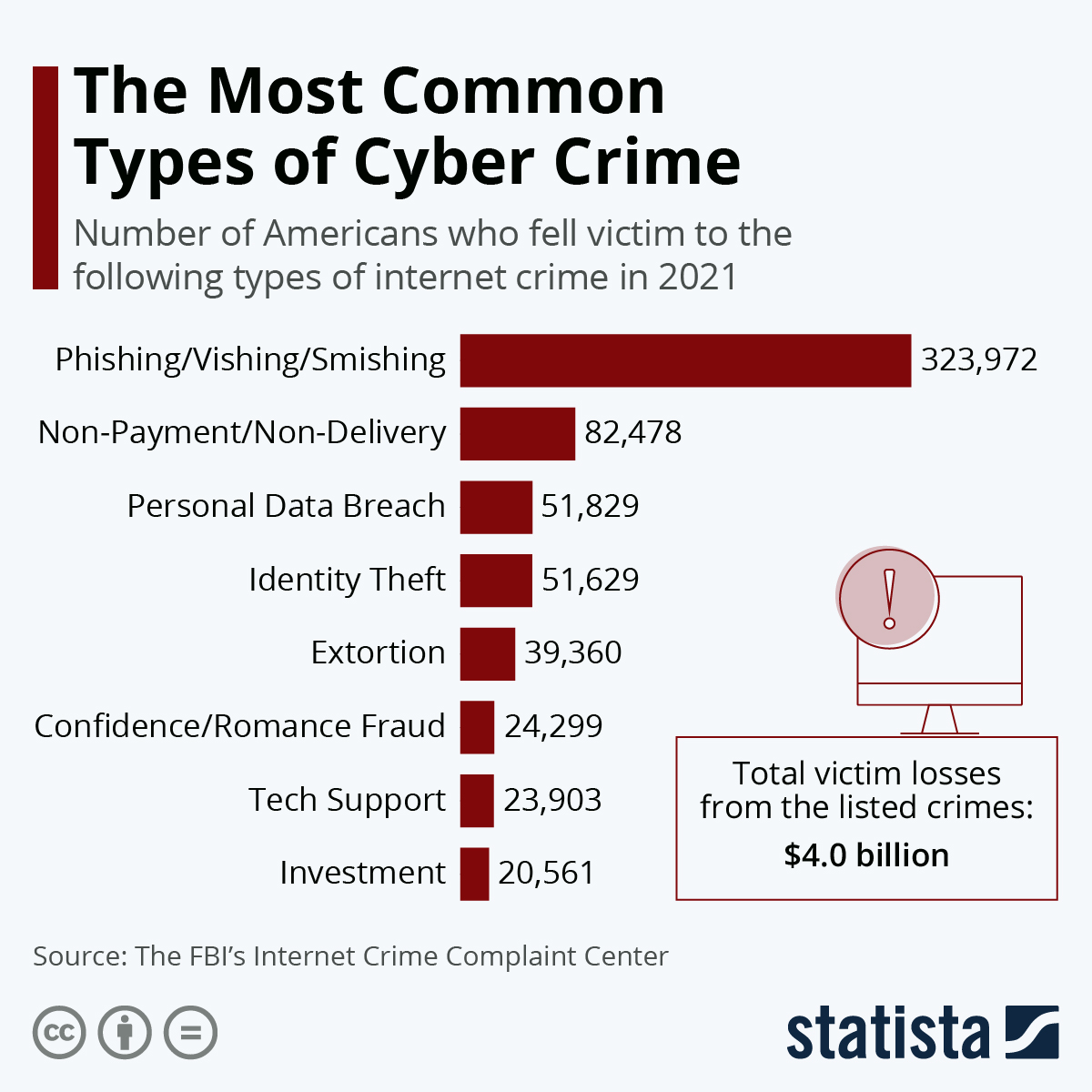
In this comprehensive guide, we will explore the concept of cybercrime and its impact on individuals, businesses, and society. From hacking and identity theft to phishing and malware attacks, we will delve into the different types of cybercrimes plaguing our digital world.
Additionally, we will uncover effective cybersecurity measures that individuals and organizations can implement to protect themselves against these threats. So, join us as we navigate the realm of cybercrime and empower ourselves with the knowledge to stay safe in an increasingly interconnected world.
Introduction to Cybercrime
Cybercrime refers to criminal activities that are conducted through the use of computers, the internet, or other digital technologies. It has become an increasingly serious issue in today’s digitally connected world, affecting individuals, businesses, and society as a whole.One of the most common types of cybercrime is hacking, where unauthorized individuals gain access to computer systems or networks to steal or manipulate sensitive information.
Ensuring cyber security is a joint effort between legislation and executive authorities. Strong laws and regulations play a vital role in protecting individuals and organizations from cyber threats. Additionally, the executive authorities are responsible for enforcing these laws and taking necessary actions against cyber criminals.
By working together, legislation and executive authorities can create a safer online environment for everyone. To know more about the importance of cyber security and the role of legislation and executive authorities, you can read this informative article .
This can lead to financial loss, privacy breaches, and even damage to a person’s reputation.Identity theft is another prevalent form of cybercrime, where personal information is stolen and used for fraudulent purposes. This can have devastating consequences for individuals, as it can result in financial ruin and the loss of their digital identities.Phishing
is a cybercrime technique where criminals deceive individuals into revealing their personal information, such as passwords or credit card numbers, by posing as trustworthy entities. This information is then used to carry out fraudulent activities.Malware attacks are also a significant concern in the world of cybercrime.
Malicious software, such as viruses, worms, or ransomware, is used to gain unauthorized access to computer systems or to cause damage to data and networks.To highlight the seriousness of cybercrime, let’s take a look at some high-profile cases. In 2017, the Equifax data breach exposed the personal information of approximately 147 million people.
This breach had far-reaching consequences, including financial losses and a loss of trust in the company’s ability to protect sensitive information.Another example is the WannaCry ransomware attack that occurred in 2017, which affected hundreds of thousands of computers worldwide. This attack encrypted data on the infected systems and demanded a ransom in exchange for the decryption key, causing significant disruption and financial losses for individuals and organizations.These
examples demonstrate the real-world impact of cybercrime and the urgent need for effective cybersecurity measures to protect individuals, businesses, and society from these threats.
Types of Cybercrimes
- Hacking: Unauthorized access to computer systems or networks to steal or manipulate information.
- Identity theft: Stealing personal information for fraudulent purposes.
- Phishing: Deceiving individuals into revealing sensitive information through fraudulent emails or websites.
- Malware attacks: Using malicious software to gain unauthorized access or cause damage to computer systems.
It is important to note that these are just a few examples of the many types of cybercrimes that exist.
Understanding Cybersecurity Measures
Cybersecurity measures are essential for individuals and organizations to protect themselves against the ever-increasing threat of cybercrimes. By implementing effective security practices, we can safeguard our data, privacy, and online presence. In this section, we will discuss some key cybersecurity measures that can help in preventing cyberattacks and minimizing the risk of becoming a victim.
Importance of Strong PasswordsOne of the fundamental steps in enhancing cybersecurity is to use strong and unique passwords. A strong password typically consists of a combination of upper and lowercase letters, numbers, and special characters. It should be at least eight characters long and avoid common phrases or personal information.
By creating strong passwords, individuals can significantly reduce the chances of unauthorized access to their accounts and sensitive information. Two-Factor Authentication (2FA)Two-factor authentication adds an extra layer of security to online accounts by requiring users to provide two forms of identification. In addition to the traditional username and password, 2FA often involves entering a unique code sent to a trusted device or using biometric data like fingerprints or facial recognition.
This additional step adds an extra barrier against unauthorized access, as even if someone manages to obtain the password, they would still need the second factor to gain entry. Regular Software UpdatesRegularly updating software is crucial for maintaining a secure digital environment.
Software updates often include security patches that fix vulnerabilities and address known issues. By keeping their operating systems, applications, and antivirus software up to date, individuals and organizations can ensure that they are protected against the latest threats and exploits.
The Role of Antivirus Software, Kejahatan siber pdf
Antivirus software plays a vital role in preventing and detecting cyberattacks. It scans files and programs for known malware signatures, identifies suspicious behavior, and removes or quarantines malicious files. It is crucial to have a reputable antivirus program installed on all devices to provide real-time protection against viruses, ransomware, spyware, and other forms of malware.
The Importance of Firewalls
Firewalls act as a barrier between a trusted internal network and external networks, such as the internet. They monitor and control incoming and outgoing network traffic, filtering out potentially harmful data packets. Firewalls can prevent unauthorized access to a network and protect against various types of cyberattacks, including malware infections and data breaches.
Cyber security is a crucial aspect in today’s digital era. With the increasing dependence on technology, protecting our online information has become more important than ever. Cyber threats such as hacking, phishing, and identity theft are constantly evolving, making it essential for individuals and organizations to stay vigilant.
Implementing strong security measures and regularly updating software are some of the ways to ensure cyber security. To learn more about the importance of cyber security, you can check out this article .
Secure Browsing Practices
Practicing secure browsing is essential for protecting against online threats. This includes being cautious when clicking on links or downloading files from untrusted sources, verifying website security certificates, and using encrypted connections (HTTPS) for sensitive transactions. Additionally, individuals should regularly clear their browsing history and cache to minimize the risk of data leakage or unauthorized access.By
implementing these cybersecurity measures, individuals and organizations can significantly reduce their vulnerability to cybercrimes. It is important to stay proactive and keep up with the latest security practices to stay one step ahead of cybercriminals.
Cybercrime Prevention Strategies for Individuals

Cybercrime is a growing concern in today’s digital age, and it is crucial for individuals to take proactive steps to protect themselves. By implementing certain strategies, you can greatly reduce the risk of falling victim to cybercrimes and safeguard your personal information.It
is important to exercise caution when sharing personal information online. Always think twice before providing sensitive details such as your full name, address, phone number, or financial information on websites or social media platforms. Limit the amount of personal information you share publicly to minimize the chances of identity theft or fraud.Another
essential aspect is being mindful of suspicious emails or links. Cybercriminals often use phishing emails or deceptive links to trick individuals into revealing their personal information or downloading malicious software. Be wary of unsolicited emails, especially those asking for sensitive information or urging immediate action.
Avoid clicking on links in emails from unknown sources and double-check the email addresses of senders to ensure they are legitimate.One important concept to understand is social engineering. This refers to the manipulation of individuals into divulging confidential information or performing actions that may compromise their security.
Cybercriminals may use various tactics, such as pretending to be a trusted entity or creating a sense of urgency, to deceive individuals. To avoid falling victim to scams, it is crucial to be vigilant and skeptical of unsolicited requests for information or assistance.
Practical Tips for Cybercrime Prevention
To protect yourself from cybercrimes, consider implementing the following strategies:
- Use strong and unique passwords for your online accounts. Avoid using easily guessable passwords and consider using a password manager to securely store your credentials.
- Enable two-factor authentication whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your mobile device, in addition to your password.
- Keep your devices and software up to date. Regularly install updates and patches to address security vulnerabilities that cybercriminals may exploit.
- Be cautious while using public Wi-Fi networks. Avoid accessing sensitive information or making online transactions when connected to public Wi-Fi, as these networks are often unsecured and can be easily compromised.
- Regularly back up your important data. In the event of a cyberattack or data loss, having backups ensures that you can restore your information without paying a ransom or losing valuable files.
Remember, prevention is key when it comes to cybercrimes. By implementing these strategies and staying vigilant, you can significantly reduce the risk of becoming a victim. Stay informed about the latest cybersecurity threats and educate yourself on best practices to stay safe online.
Cybercrime Prevention Strategies for Businesses: Kejahatan Siber Pdf
In today’s digital age, businesses face numerous cybersecurity challenges that can have devastating consequences if not adequately addressed. Cyberattacks can result in financial losses, reputational damage, and even legal implications. Therefore, it is crucial for businesses to implement effective cybersecurity measures to protect their sensitive information and mitigate the risks associated with cybercrime.
The Importance of Regular Security Audits
Regular security audits are essential for businesses to identify vulnerabilities in their networks and systems. By conducting these audits, businesses can proactively detect and address any weaknesses or potential entry points that cybercriminals may exploit. This includes evaluating the effectiveness of firewalls, antivirus software, and intrusion detection systems.
Security audits also help ensure that businesses are compliant with industry regulations and standards.
Implementing Employee Training Programs
Employees play a significant role in maintaining the cybersecurity of a business. It is crucial for businesses to provide comprehensive training programs to educate employees about the importance of cybersecurity and the best practices to follow. This includes raising awareness about phishing attacks, social engineering tactics, and the proper handling of sensitive information.
By empowering employees with the knowledge to identify and respond to potential threats, businesses can significantly reduce the risk of successful cyberattacks.
Establishing Incident Response Plans
In the event of a cyberattack, it is vital for businesses to have well-defined incident response plans. These plans Artikel the steps to be taken in the event of a breach, ensuring a swift and effective response to mitigate the damage.
Incident response plans should include procedures for isolating affected systems, notifying relevant stakeholders, and engaging cybersecurity experts to investigate and remediate the attack. Regularly testing and updating these plans is essential to adapt to new and evolving cyber threats.
The Significance of Data Encryption
Data encryption is a fundamental component of cybersecurity for businesses. By encrypting sensitive data, businesses ensure that even if it is intercepted by cybercriminals, it remains unintelligible and unusable. This is especially important for data that is stored or transmitted across networks.
Implementing robust encryption algorithms and protocols safeguards confidential information and protects businesses from unauthorized access.
Secure Network Configurations
Configuring networks securely is essential to prevent unauthorized access and protect against cyberattacks. Businesses should implement strong passwords, regularly update network devices, and restrict access to sensitive systems. Additionally, employing intrusion detection and prevention systems can help detect and block malicious activities within the network.
By implementing secure network configurations, businesses can significantly reduce the risk of successful cyber intrusions.
The Importance of Secure Backup Systems
Secure backup systems are crucial for businesses to recover from a cyberattack effectively. Regularly backing up critical data ensures that even if it is compromised or lost due to a cyber incident, businesses can quickly restore their operations without significant disruptions.
It is essential for businesses to store backups in secure offsite locations and regularly test the restoration process to ensure its effectiveness.By implementing these cybercrime prevention strategies, businesses can enhance their cybersecurity defenses and reduce the risk of falling victim to cyberattacks.
However, it is important to stay vigilant, as cybercriminals continue to evolve their tactics. Regularly updating and adapting cybersecurity measures is crucial to stay one step ahead in the ongoing battle against cybercrime.
Government Initiatives and International Cooperation against Cybercrime
The increasing threat of cybercrime has prompted governments and international organizations to take proactive measures to combat this global issue. Through collaborative efforts and information sharing, they aim to enhance cybersecurity and protect individuals and businesses from cyber threats.Law enforcement agencies play a crucial role in investigating and prosecuting cybercriminals.
They utilize advanced technological tools and techniques to track down cybercriminals, gather evidence, and bring them to justice. These agencies work closely with cybersecurity experts and legal professionals to ensure that cybercrimes are thoroughly investigated and the perpetrators are held accountable for their actions.International
cooperation is vital in addressing cybercrimes that transcend national borders. Cybercriminals often operate from different countries, making it challenging to apprehend them within a single jurisdiction. By collaborating with other countries, law enforcement agencies can share information, intelligence, and best practices to effectively combat cybercrime on a global scale.
This cooperation also enables them to coordinate efforts in apprehending and extraditing cybercriminals, ensuring that they face legal consequences for their actions regardless of their location.In addition to government initiatives, international organizations such as INTERPOL and the United Nations have established programs and initiatives to combat cybercrime.
These organizations facilitate cooperation among member countries, provide training and capacity-building programs, and promote the development of international legal frameworks to address cybercrime effectively.
Efforts Taken by Governments
Governments worldwide have recognized the severity of cybercrimes and have implemented various initiatives to combat them. These efforts include:
- Enacting laws and regulations: Governments have enacted legislation and regulations that define cybercrimes, establish penalties for offenders, and provide a legal framework for investigating and prosecuting cybercriminals.
- Establishing cybercrime units: Many countries have established specialized cybercrime units within their law enforcement agencies. These units are equipped with the necessary expertise and resources to handle cybercrime cases effectively.
- Investing in cybersecurity infrastructure: Governments allocate significant resources to enhance their cybersecurity infrastructure. This includes developing advanced technologies, establishing secure communication networks, and implementing robust cybersecurity measures to protect critical infrastructure.
- Collaborating with private sector and academia: Governments collaborate with the private sector and academia to leverage their expertise in cybersecurity. This partnership fosters innovation, knowledge sharing, and the development of cutting-edge technologies to counter cyber threats.
International Cooperation and Information Sharing
International cooperation and information sharing are essential in combating cybercrimes that transcend national boundaries. Some key initiatives include:
- Establishment of international cybercrime centers: Organizations such as INTERPOL have established specialized centers to facilitate international cooperation in combating cybercrime. These centers serve as hubs for sharing intelligence, coordinating operations, and conducting joint investigations.
- Mutual legal assistance treaties (MLATs): MLATs are agreements between countries that enable them to request and provide assistance in investigating and prosecuting cybercrimes. These treaties streamline the process of obtaining evidence and extraditing cybercriminals across borders.
- Information sharing platforms: Governments and law enforcement agencies participate in information sharing platforms to exchange intelligence, best practices, and threat indicators. These platforms enable timely detection and response to cyber threats.
- Capacity-building programs: International organizations conduct capacity-building programs to enhance the cybersecurity capabilities of member countries. These programs provide training, technical assistance, and knowledge sharing to strengthen the ability to prevent, detect, and respond to cybercrimes.
By implementing these initiatives and fostering international cooperation, governments and international organizations are making significant strides in combating cybercrimes. However, the evolving nature of cyber threats requires continuous efforts and collaboration to stay ahead of cybercriminals and protect individuals, businesses, and critical infrastructures from cyber attacks.
Summary
In conclusion, kejahatan siber pdf sheds light on the pressing issue of cybercrime and equips readers with valuable insights into safeguarding their digital lives. By understanding the various types of cybercrimes and implementing robust cybersecurity measures, individuals and businesses can fortify their defenses against malicious actors.
Furthermore, the importance of government initiatives and international cooperation in combating cybercrimes cannot be overstated. Let us all work together to create a safer and more secure digital landscape for everyone.
FAQ
What are some common cybercrimes?
Common cybercrimes include hacking, identity theft, phishing, and malware attacks. These malicious activities pose significant threats to individuals and organizations alike, compromising sensitive information and causing financial losses.
How can individuals protect themselves from cybercrimes?
Individuals can protect themselves from cybercrimes by being cautious about sharing personal information online, avoiding suspicious emails or links, and recognizing and avoiding scams. It is also crucial to use strong passwords, enable two-factor authentication, and keep software up to date.
Additionally, practicing secure browsing habits and using antivirus software and firewalls can help prevent cyberattacks.
What cybersecurity measures should businesses implement?
Businesses should enhance their cybersecurity defenses by conducting regular security audits, implementing employee training programs, and establishing incident response plans. Data encryption, secure network configurations, and secure backup systems are also vital. By prioritizing cybersecurity, businesses can mitigate the risks of cyberattacks and protect their valuable data and assets.
